IP address is a unique address of each network card with the help of which each computer is
identified on the network.
All nodes in a TCP/IP network (clients, servers, routers, etc.) are assigned an "IP address,"
which is written as four numbers between dots, such as 193.4.64.01. The first part of the address is the
network address, and the second part is the host (station) address, also known as the net ID and host
ID. The network address allows TCP/IP packets to be routed to a different network. The number of
bytes used for the net ID and host ID vary according to a class system, and the first three bits of the
first byte determine this ratio.
There are two versions of IP address that is available and is known as ipv4 and ipv6.The reason
for introduction of ipv6 is to increase in no of public IP address which ipv4 is not able to provide due to exponential growth of computers.
address is classified in various category and they are:
1. Class A - Only the first octet is used for addressing and There first octets lies in between 1 to 126
2. Class B - The first two octet are used for addressing and the balance used for hosts. There first octets lies in between 128 to 191
3. Class C - The first three octet are used for There first octets lies in between 192 to 223.
4. Class D - There first octets lies in between 224 to 239.these are used for multicasting
5. Class E - There first octets lies in between 240 to 255.this class is exclusively used for R & D future use.
Loopback IP – 127.0.0.1
10.0.0.0 to 10.255.255.255 in class A 172.16.0.0 to 172.31.254.255 in class
B and 192.168.0.0 to 192.168.255.255 in class C is known as Private IP address and may
be used for private Networks.
Network ID – 0.0.0.0 is known as network id.
Broadcast ID – 255.255.255.255 is known as broadcast ID
IP version 6
IPv6 is the new standard protocol for the Internet. Windows Vista, Apple Computer's Mac OS
X, and an increasing range of Linux distributions include native support for the protocol, but it is not
yet widely deployed elsewhere.
Addresses are 128 bits (16 bytes) wide, which, even with a generous assignment of netblocks, will more than suffice for the foreseeable future. In theory, there would be exactly 2128, or about 3.403 × 1038 unique host interface addresses. Further, this large address space will be sparsely populated, which makes it possible to again encode more routing information into the addresses themselves.
Example: 2001:0db8:85a3:08d3:1319:8a2e:0370:7334
1. Current IP Address = 4 x 8-Bit
• 4,294,467,295 addresses
2. Version 6 IP Address = 8 x 16-Bit
• 3 x1038 approx addresses
This ‘should provide sufficient addresses for our future needs’ – however, it is suggested that before long even the light switches in our homes will need their own IP addresses.
Format – hexadecimal numbers separated by colons e.g 4718:25E1:4450:C287:0018:52F3:B5C2:001F
IP version 6 private addresses
Just as there are addresses for private, or internal networks in IPv4 (one example being the 192.168.0.0 - 192.168.255.255 range), there are blocks of addresses set aside in IPv6 for private addresses. Addresses starting with FE80: are called link-local addresses and are routable only on your local link area. This means that if several hosts connect to each other through a hub or switch then they would communicate through their link-local IPv6 address.
IP address subnetting
Both IPv4 and IPv6 addresses utilize subnetting, or dividing the IP address into two parts: the network address and the host address. By using a subnet mask, the computer can determine where to split the IP address.
Static and dynamic IP addresses
When a computer uses the same IP address every time it connects to the network, it is known as a Static IP address. In contrast, in situations when the computer's IP address changes frequently (such as when a user logs on to a network through dialup or through shared residential cable) it is called a Dynamic IP address.
Method of assigning
Static IP addresses are manually assigned to a computer by an administrator, either through the operating system configuration or through a command (e.g. ipconfig or ifconfig). This contrasts with dynamic IP addresses, where an IP address is automatically assigned to a computer by a remote server which is acting as a Dynamic Host Configuration Protocol server. Even through IP addresses assigned using DHCP may stay the same for long periods of time, they are liable to change depending on the addresses available in the set scope of DHCP server.
Uses of dynamic addressing
Dynamic IP Addresses assigned, on LANs or most broadband networks, by Dynamic Host Configuration Protocol (DHCP) servers are used because it reduces the administrative burden of assigning static addresses within a network. In most desktop operating systems, dynamic IP configuration is enabled by default.
Uses of static addressing
Static addressing is essential in some infrastructure situations, such as finding the Domain Name Service directory host that will translate domain names to numbers (IP addresses). Static addresses are also convenient, but not absolutely necessary, to locate servers inside an enterprise. An address obtained from a DNS server comes with a time to live, or caching time, after which it should be looked up to confirm that it has not changed. Even static IP addresses do change as a result of network administration.
Data Link Layer
1. Has two sub layers of its own:
a. Logical Link Control (LLC)
b. Media Access Control (MAC)
2. LLC acts between protocols such as Internet Protocol (IP) and the MAC method.
3. MAC is responsible for the connection to the physical media (eg cable)
4. The data link layer takes raw transmission and transform it into a line that appears free of Transmission errors in the network layer.
5. The Data-Link Layer also is where we would find the MAC Address. (Media Access Control). To find the MAC Address of your computer, or any computer: Start/Programs/MS Prompt and type: ipconfig/all
6. MAC: - Each NIC has a unique number hard coded in to the card – its physical address. The first 6 digits denote the manufacturer, the next six are unique) When the MAC address is added to the packet it is now known as a frame. It now has all the information required to travel from the source to the destination
7. we also find smart devices such as switches in the Data-Link Layer
8. The digital information that needs to be sent such as and e-mail, attachments, etc needs to be broken into smaller bits known as packets. These packets require some information similar to sending a letter in the mail.
Physical Layer
1. The lowest, bottom, layer – responsible for the physical connection between devices
2. The NIC converts the data (bits) in to transmission signals.
3. Transmissions may be analogue or digital
4. Responsible for the rate of transmission
5. Includes all components such as the type of connector (RJ-45, Token Ring, BNC, SC connector)
6. Devices at this level include NICs, repeaters, hubs and concentrators
7. The physical layer is concerned with transmitting raw bits over a communication channel though hubs, wires (cat5UTP), modems, network cards… basically anything that is physical to the network
8. When looking at network cables, there are 2 types that affect nodes. They are:
a) Straight though cables or also known as patch cables. They are used where two different types of devices requires to be connected. Like a computer from a switch.
b) Cross-over cables. They are used where two similar types of devices requires to be connected. Like a switch from another switch.
TCP/IP *(for advance Readers only)
TCP/IP is composed of two parts: TCP (Transmission Control Protocol) and IP (Internet Protocol). TCP is a connection-oriented protocol that passes its data to IP, which is connectionless. TCP sets up a connection at both ends and guarantees reliable delivery of the full message sent. TCP tests for errors and requests retransmission if necessary, because IP does not.
TCP/IP is a robust and proven technology that was first tested in the early 1980s on ARPAnet, the U.S. military's Advanced Research Projects Agency network, the world's first packet-switched network. TCP/IP was designed as an open protocol that would enable all types of computers to transmit data to each other via a common communications language.
The immense influence of the Internet caused its communications protocol to become the world standard. Almost all networks, except for the circuit-switched networks of the telephone companies, have migrated to TCP/IP.
Multiple Layers
TCP/IP is a layered protocol, which means that after an application initiates the communications, the message (data) to be transmitted is passed through a number of software stages, or layers, until it actually moves out onto the wire, or if wireless, into the air. The data are packaged with a different header at each layer. At the receiving end, the corresponding software at each protocol layer unpackages the data, moving it "back up the stack" to the receiving application.
TCP and IP
TCP/IP is composed of two parts: TCP (Transmission Control Protocol) and IP (Internet Protocol). TCP is a connection-oriented protocol that passes its data to IP, which is connectionless. TCP sets up a connection at both ends and guarantees reliable delivery of the full message sent. TCP tests for errors and requests retransmission if necessary, because IP does not.
UDP
An alternative protocol to TCP within the TCP/IP suite is UDP (User Datagram Protocol), which does not guarantee delivery. Like IP, UDP is also connectionless, but very useful for transmitting audio and video that is immediately heard or viewed at the other end. If packets are lost in a UDP transmission (they can be dropped at any router junction due to congestion), there is neither time nor
a need to retransmit them. A momentary blip in a voice or video transmission is not critical.
Application Layer 7
The top layer of the protocol stack is the Application Layer. It refers to the programs that initiate the communications in the first place. TCP/IP includes several Application Layer protocols for mail, file transfer, remote access, authentication and name resolution. These protocols are embodied in programs that operate at the top layer just like any custom-made or packaged client/server application.
FTP, SMTP, Telnet, DNS and WINS
Some of the most widely known application protocols in the TCP/IP suite are FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), Telnet, DNS (Domain Name System) and WINS (Windows Internet Name System). FTP programs are widely used to copy files across the network. All
TCP/IP-based mail programs use SMTP to send e-mail. Telnet is a terminal emulator that provides access to a remote host. DNS and WINS allow hosts to be given understandable names, and the DNS and WINS servers turn those names into the IP address required by TCP/IP networks.
Other Client/Server Applications
The language and format in a user's proprietary client/server program are not known to
TCP/IP. They are known only to the sending and receiving programs that must communicate with each
other. The data from all applications, whether a proprietary program or part of the TCP/IP suite (FTP,
Telnet, etc.), are "handed down" from the Application Layer in the client to the lower layers in the
stack for transport. At the server side, they are "handed up" the stack to the appropriate application
for processing. The operation is reversed for data sent back from the server to the client.
IP Addresses
All nodes in a TCP/IP network (clients, servers, routers, etc.) are assigned an "IP address,"
which is written as four numbers between dots, such as 193.4.64.01. The first part of the address is the
network address, and the second part is the host (station) address, also known as the netid and hostid.
The network address allows TCP/IP packets to be routed to a different network. The number of bytes
used for the netid and hostid vary according to a class system, and the first three bits of the first byte
determine this ratio (see IP address for details).
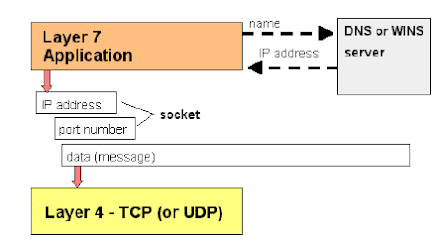
Ports and Sockets
A program identifies the program it wishes to communicate with by its socket, which is a combination of (1) the server's IP address and (2) the program's port. If it does not know the IP address, but knows the server by name, it uses a Domain Name System server (DNS server) to turn the name into the IP address. In Windows networks, a Windows Internet Name System server (WINS server) is used to map NetBIOS names, which are assigned to many Windows machines in small networks, to IP addresses.
The port is a logical number assigned to every application. For FTP, SMTP, HTTP (Web) and other common applications, there are agreed-upon numbers known as "well-known ports." For example, HTTP applications on the Web are on port 80, so a Web server is located by its IP address and port 80. An organization's internal client/server applications are given arbitrary ports for their ownpurposes.
OSI Layers 5, 6 & 7 Are All in the Top Layer
OSI Layers 5, 6 and 7 are all included in TCP/IP's Application Layer. For example, OSI Layer 6
(Presentation Layer) is where data conversion (ASCII to EBCDIC, floating point to binary, etc.) and
encryption/decryption are performed. OSI Layer 5 is the Session Layer, which is performed in Layer 4 in TCP/IP. Thus we jump from Layer 7 down to Layer 4.
From Application to Transport Layer
The application delivers its data to the communications system by passing a stream of data
bytes to the transport layer along with the socket of the destination machine. The dotted lines in this
diagram are conceptual. DNS and WINS requests go down the stack (in a UDP packet) like everything
else in order to go out onto the network
Transport Layer 4 - TCP & UDP
TCP establishes a connection at both ends, creating a "virtual connection" between the two
machines before any data can be transmitted. Once established, both sides negotiate the maximum
size of a TCP packet. Although TCP supports packets up to 64KB, in most cases, the size will be based on the underlying network, such as Ethernet, which can hold a maximum of 1518 bytes. Token Ring and FDDI support larger frames. TCP attaches a header onto the packet that contains the source and destination ports as well as the sequence number of the packet, and it hands it over to IP along with the destination IP address. (A TCP packet is technically a Protocol Data Unit or segment, but is more often called a packet in common parlance.)
The Sliding Window
TCP uses a sliding window system, which is an adjustable buffer that allows a number of packets to be received before an acknowledgment is sent back. The size of the window can be changed as conditions change, and TCP handles this "flow control" in real time. It also handles the retransmission of packets that have been received with errors.
UDP (User Datagram Protocol)
UDP is an alternative to TCP that does not establish a connection, makes no guarantees and provides no flow control or error detection. Either it does not matter as would be the case for real-time audio or video, or the application programs using UDP must themselves include the error detection and recovery that TCP provides.
From Transport to Network Layer
TCP and UDP hand over their packets to IP along with the IP address of the destination node.
The packet size is typically the size of the underlying data link layer such as Ethernet or Token Ring
Network (Internet) Layer 3 - IP
The IP protocol accepts the packets from TCP or UDP and prepares them for the Data Link
Layer below by turning the IP addresses into physical station addresses (MAC addresses) and fragmenting the packets (if necessary) into the required frame size. IP uses the ARP (Address Resolution Protocol) to obtain the MAC address, unless (1) the address has already been ARP'd and is
in the cache or (2) there is a predefined configuration file that contains the addresses. An ARP request
is broadcast onto the network, and the machine with that IP address responds with its MAC address. If
the target machine is in a different network or subnetwork than the source machine, IP supplies the target address of the default gateway, which is the router that can direct the packet to the appropriate network.
Datagrams
IP outputs packets called "datagrams," and each datagram is prefixed with an IP header that contains source and destination IP addresses. If IP has to fragment the packet further, it creates multiple datagrams with sequence numbers so that they can be reassembled by IP on the other end. IP hands over each datagram to the data link layer below along with the MAC address (Ethernet address) of the target station or router.
Multicast
IP supports a very useful feature called "multicast," which allows one message to be delivered to multiple recipients. That means one IP data stream can travel a long, circuitous route before it is fanned out to all the target stations by the last router.
From Network to Data Link Layer
IP datagram are handed over to Ethernet, Token Ring, ATM or some other data link protocol responsible for moving the data across the wire. The dotted lines in the diagram are conceptual. ARP
requests go down the stack like everything else in order to go out onto the network.
IP Is the Routing Mechanism
In a large enterprise or on the Internet, the IP protocol is used to route the packets from network to network. Routers contain routing tables that move the datagrams to the next "hop," which is either the destination network or another router. Datagrams can traverse several routers within an enterprise and dozens of routers over the Internet.
Fragmentation
Routers that span different types of networks may have to fragment the datagrams even further if they direct them onto routes that use a smaller frame size than the incoming frame; for example, from FDDI to Ethernet.
From Hop to Hop
Routers inspect only the network portion (netid) of the address and direct the incoming datagrams to the appropriate outgoing port for the next hop. Routers move datagrams from one hop to the next as they are mostly aware of only the devices that are directly connected to them. Eventually, if the routing tables are correctly updated, the datagrams reach their destination. Routers use routing protocols to obtain current routing information about the networks and hosts that are directly connected to them.
Routing Table Example
If a router receives packets for a remote network, it sends them out the port that will reach the next router. Router ports are entirely different than socket ports. Router ports are physical pathways to and from the router connected via cable. Socket ports are logical assignments made to running programs.
Data Link Layer 2 - Ethernet
IP can connect directly to Ethernet, Token Ring, FDDI, ATM, SONET, X.25, frame relay and other networks. Since Ethernet is the most widely used data link protocol, or network access method, we use it in our example. Ethernet wraps the IP datagrams into its own frame format, which includes a header
with source and destination MAC addresses (station addresses) and a trailer that contains checksum data.
Ethernet Packets Can Collide
Ethernet uses the CSMA/CD (carrier sense multiple access/collision detection) access method to broadcast the frames onto the wire. If two stations transmit at the same time, their frames collide, and they each back off and wait a random amount of time before trying again (in milliseconds). The data link layer is responsible for reliable node to node transmission. If an Ethernet frame is received with errors, Ethernet handles retransmission until it is received error free.
LAN to WAN
If IP datagrams start out in a LAN, go to a wide area network (WAN) and then to a LAN at the other side, the Ethernet LAN frames are converted into WAN frames by a router and back again to Ethernet frames by the router at the other side.
Onto the Wire
The data link layer is responsible for reliable node to node transmission within a sub network. When Ethernet frames traverse several routers, the same frames are retransmitted over again by the next router.
Packets, Datagrams or Frames?
The message starts out in one host, goes down the protocol stack, over the wire, and back up the stack on the receiving host. The counterpart protocols unpackage the frames, datagrams and packets and deliver the data to the application for processing.
Although the terms are technically TCP segments, IP datagrams and Ethernet frames, they all ride over packet-switched networks and are frequently called packets at all stages.
IP Is "The" Standard
IP has become the worldwide standard protocol for all forms of electronic communications, including data, voice and video. The amount of data communications is increasing far more than voice traffic, and it is expected that all data, voice and video will ride over IP-based networks in the future.
Transporting IP
Transporting IP packets over a LAN is typically done via Ethernet. Over the WAN, IP generally rides over SONET or on ATM on top of SONET. In the future, IP is expected to ride directly over DWDM
fiber
Various Protocol in brief
1) HTTP - Hyper Text Transfer Protocol. HTTP takes care of the communication between a web server
and a web browser.HTTP is used for sending requests from a web client (a browser) to a web server,
returning web content (web pages) from the server back to the client.
2) HTTPS - Secure HTTP.HTTPS takes care of secure communication between a web server and a web
browser. HTTPS typically handles credit card transactions and other sensitive data.
3) SSL - Secure Sockets Layer. The SSL protocol is used for encryption of data for secure data
transmission.
4) SMTP - Simple Mail Transfer Protocol. SMTP is used for transmission of e-mails.
5) MIME - Multi-purpose Internet Mail Extensions. The MIME protocol lets SMTP transmit multimedia
files including voice, audio, and binary data across TCP/IP networks.
6) IMAP - Internet Message Access Protocol. IMAP is used for storing and retrieving e-mails.
7) POP - Post Office Protocol.POP is used for downloading e-mails from an e-mail server to a personal
computer.
8) FTP - File Transfer Protocol.FTP takes care of transmission of files between computers.
9) NTP - Network Time Protocol.NTP is used to synchronize the time (the clock) between computers.
10) DHCP - Dynamic Host Configuration Protocol. DHCP is used for allocation of dynamic IP addresses to computers in a network.
11) SNMP - Simple Network Management Protocol. SNMP is used for administration of computer
networks.
12) LDAP - Lightweight Directory Access Protocol. LDAP is used for collecting information about users and
e-mail addresses from the internet.
13) ICMP - Internet Control Message Protocol. ICMP takes care of error handling in the network.
14) ARP - Address Resolution Protocol.ARP is used by IP to find the hardware address of a computer
network card based on the IP address.
15) RARP - Reverse Address Resolution Protocol. RARP is used by IP to find the IP address based on the hardware address of a computer network card.
16) BOOTP - Boot Protocol. BOOTP is used for booting (starting) computers from the network.
17) PPTP - Point to Point Tunneling Protocol. PPTP is used for setting up a connection (tunnel) between private networks.
18) UDP -An alternative protocol to TCP within the TCP/IP suite is UDP (User Datagram Protocol), which does not guarantee delivery. Like IP, UDP is also connectionless, but very useful for transmitting audio and video that is immediately heard or viewed at the other end. If packets are lost in a UDP transmission (they can be dropped at any router junction due to congestion), there is neither time nor
a need to retransmit them. A momentary blip in a voice or video transmission is not critical.
19) FTP, SMTP, Telnet, DNS and WINS -Some of the most widely known application protocols in the TCP/IP suite are FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol), Telnet, DNS (Domain Name System) and WINS (Windows Internet Name System). FTP programs are widely used to copy files across the network. All TCP/IP-based mail programs use SMTP to send e-mail. Telnet is a terminal emulator that provides access to a remote host. DNS and WINS allow hosts to be given understandable names, and the DNS and WINS servers turn those names into the IP address required by TCP/IP networks.
20) Ports and Sockets -A program identifies the program it wishes to communicate with by its socket,
which is a combination of (1) the server's IP address and (2) the program's port. If it does not know the
IP address, but knows the server by name, it uses a Domain Name System server (DNS server) to turn the name into the IP address. In Windows networks, a Windows Internet Name System server (WINS server) is used to map NetBIOS names, which are assigned to many Windows machines in small networks, to IP addresses.
The port is a logical number assigned to every application. For FTP, SMTP, HTTP (Web) and other common applications, there are agreed-upon numbers known as "well-known ports." For example, HTTP applications on the Web are on port 80, so a Web server is located by its IP address and port 80. An organization's internal client/server applications are given arbitrary ports for their own
purposes.
अन्य विषय
- INTRODUCTION TO COMPUTERS
- What is Software
- GENERATION OF COMPUTERS
- CLASSIFICATION AND TYPES OF COMPUTERS
- FUNDAMENTALS OF OPERATING SYSTEM
- FUNDAMENTALS OF OPERATING SYSTEM
- INTRODUCTION OF VARIOUS DATA PASSING SCHEMES
- How Token Ring Works
- BASIC MEMORY ARCHITECTURE INTRODUCTION
- TYPES OF RAM AND ROM
- PHYSICAL AND VIRTUAL MEMORY
- STORAGE DEVICES INTRODUCTION
- BUS ARCHITECTURE
- INTRODUCTION WITH VARIOUS EXPANSION BUS/SL INTRODUCTION WITH VARIOUS EXPANSION BUS/SLOTS
- PCI EXPRESS
- UNIVERSAL SERIAL BUS
- FIRE WIRE IEEE 1394
- AMR AND CNR
- BIOS
- What is MICROPROCESSORS MICROPROCESSOR
- Clock Speed
- GENERATION OF PROCESSOR
- INTRODUCTION TO JUMPERS AND DIP SWITCHES
- INTRODUCTION AND IDENTIFICATION OF VARIOUS CABLE, PORTS AND CONNECTORS
- VARIOUS TYPES OF CABLES
- INTRODUCTION OF VARIOUS TYPES OF input DEVICES
- LASER PRINTER
- MONITORS
- MAINTENANCE & TROUBLESHOOTING OF COMPUTER
- BASICS OF NETWORKING, ITS TYPES
- NETWORK ARCHITECTURE & NETWORK TOPOLOGY
- Steps involved in transmission between any two computers
- Networking layers
- IP Address
- Novell netware & window NT
- UNDERSTANDING INTERNET ADDRESSES IP ADDRES
- NETWORK HARDWARE
- How a Fiber Optic Cable Works
- WINDOW SERVER 2003
- FUDAMENTALS OF SERVER
- BASIC NETWORK ADMINISTRATION
- INTRODUCTION OF INTERNET
- INTRODUCTION OF DBMS
- COMPUTER SECURITY & VIRUSES
- WEB HOSTING
- कंप्यूटर : सामान्य ज्ञान
- विभिन्न डेटा पास होने योजना
- ईथरनेट
- टक्कर की पहचान
- फ्रेम्स
- Most Ethernets Use Twisted Pairs
- साझा या स्विच
- ईथरनेट या 802.3?
- फुल-डुप्लेक्स ईथरनेट
- राउटर: लॉजिकल सेगमेंटेशन
- ईथरनेट शब्दावली
- प्रोटोकॉल
- ईथरनेट कैसे काम करता है
- मदर बोर्ड / Motherboard
- ऑपरेटिंग सिस्टम क्या है ?
- कंप्यूटर के प्रकार
- कंप्यूटर निर्माण की पीढियां
- सॉफ्टवेयर क्या है
- हार्डवेयर क्या होता है
- एक कंप्यूटर की विशेषताएँ
- मुख्य स्मृति,सहायक / माध्यमिक स्मृति
- Arithmetic and logic unit (ALU) ,Control unit
- इनपुट डिवाइस और आउटपुट डिवाइस क्या होती है
- कम्प्यूटर क्या है?
- Computer Basic Short Cut Key
- Full Form Related to computer
- Computer Exam Practice-06 Operating System
- Exam practice 05 (Microsoft Window)
- Computer Exam Practice - 4(b) Computer Function
- Computer Exam Practice 04 (a)
- Computer Objective Quetions 03
- Computee Objective type quetion 02
- Computer Objective Quetion 01
- How are Data Stored
- What is Computer Memory
- How Does a Computer Process Information
- How Does the Software Work
- Anatomy of computer
- Computers & Memory
- Type of computer & use
- Computer Generation
अन्य जानकारी
- कंप्यूटर ज्ञान
- जीव विज्ञान
- भौतिक विज्ञान
- रसायन विज्ञान
- भूगोल
- इतिहास
- उत्तराखंड सामान्य ज्ञान
- करंट अफेयर
- भारतीय फौज के बहादुरों की कहानी
- धार्मिक स्थल
- दर्शनीय स्थल
- उत्तराखंड समाचार
- उत्तराखंड की फोटो
- नई शिक्षा निति
- भरतु की ब्वारी के किस्से - नवल खाली
- ACTRESS PHOTO
- UTTRAKHAND PHOTO GALLERY
- UTTRAKHANDI VIDEO
- JOB ALERTS
- FORTS IN INDIA
- THE HINDU NEWS IN HINDI
- उत्तराखंड से सम्बंधित अन्य कोई भी जानकारी (euttra.com)
- Govt Schemes









Follow Us